
CISO Insights: Voices in Cybersecurity
No se pudo agregar al carrito
Solo puedes tener X títulos en el carrito para realizar el pago.
Add to Cart failed.
Por favor prueba de nuevo más tarde
Error al Agregar a Lista de Deseos.
Por favor prueba de nuevo más tarde
Error al eliminar de la lista de deseos.
Por favor prueba de nuevo más tarde
Error al añadir a tu biblioteca
Por favor intenta de nuevo
Error al seguir el podcast
Intenta nuevamente
Error al dejar de seguir el podcast
Intenta nuevamente
-
Narrado por:
-
De:
-
CISO Marketplace
Where Security Leaders Shape Tomorrow’s Defenses
Join us for CISO Insights, the definitive podcast for cybersecurity executives navigating today’s evolving threat landscape. Each episode delivers exclusive conversations with industry pioneers and practical frameworks from security leaders.
CISO Insights provides actionable intelligence for executives building resilient security programs. We cover everything from board-level risk communication to threat detection, compliance, and talent development.
Whether you’re a CISO, aspiring security leader, or technology executive, we equip you with the tools to thrive in a complex digital environment.
Connect with us:
Shop: cisomarketplace.com
News: threatwatch.news
Podcast: cisoinsights.show
Tools: microsec.tools
AI Resources: cybersecuritygpt.store
Follow us:
TikTok @cisomarketplace - Quick insights and security tips
YouTube @cisomarketplace - In-depth discussions and CISO interviews
Tiktok & Youtube: @ScamwatchHQ
Powered by grit, fueled by caffeine. Thanks for keeping us going!
coff.ee/cisomarketplace
coindrop.to/cisomarketplaceCopyright 2025 All rights reserved.
Episodios
-
 43 m
43 mNo se pudo agregar al carrito
Solo puedes tener X títulos en el carrito para realizar el pago.Add to Cart failed.
Por favor prueba de nuevo más tardeError al Agregar a Lista de Deseos.
Por favor prueba de nuevo más tardeError al eliminar de la lista de deseos.
Por favor prueba de nuevo más tardeError al añadir a tu biblioteca
Por favor intenta de nuevoError al seguir el podcast
Intenta nuevamenteError al dejar de seguir el podcast
Intenta nuevamente -
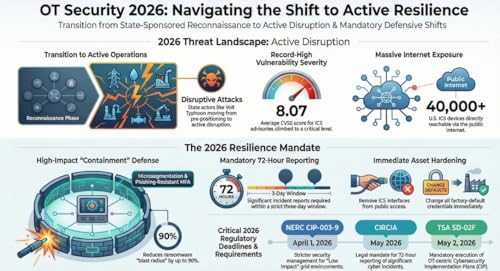 57 m
57 mNo se pudo agregar al carrito
Solo puedes tener X títulos en el carrito para realizar el pago.Add to Cart failed.
Por favor prueba de nuevo más tardeError al Agregar a Lista de Deseos.
Por favor prueba de nuevo más tardeError al eliminar de la lista de deseos.
Por favor prueba de nuevo más tardeError al añadir a tu biblioteca
Por favor intenta de nuevoError al seguir el podcast
Intenta nuevamenteError al dejar de seguir el podcast
Intenta nuevamente -
 53 m
53 mNo se pudo agregar al carrito
Solo puedes tener X títulos en el carrito para realizar el pago.Add to Cart failed.
Por favor prueba de nuevo más tardeError al Agregar a Lista de Deseos.
Por favor prueba de nuevo más tardeError al eliminar de la lista de deseos.
Por favor prueba de nuevo más tardeError al añadir a tu biblioteca
Por favor intenta de nuevoError al seguir el podcast
Intenta nuevamenteError al dejar de seguir el podcast
Intenta nuevamente
Todavía no hay opiniones


